Masking a private key/CERTICOM – T 0556/ 14 – 28 July 2016
In this decision in a patent a method of masking a privat key is claimed. It is considered not to be a mathematical method as such, because storing on a smartcard (hardware) was claimed. The claimed method achieves some protection against power analysis attacks and thus have a technical effect...
Koprozessor zur modularen Inversion/GIESECKE & DEVRIENT – T 2318/08 – 23. Mai 2012
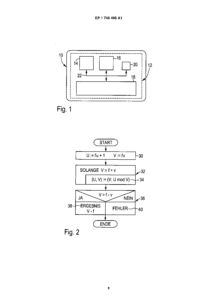
This decision provides a known cryptographic coprocessor and a known Euclidean method. However, it is not known how to use free bit sections in the coprocessor to speed up the method. Therefore, the clever use of a known coprocessor to speed up the implementation of an equally known method solves...
Edge Detection – T 0165/ 12 – 6 July 2017
In this decision, the Board found that the description of the main request did not support the claim, as the description disclosed only one specific example of a merely general feature (“first phase congruency component”). In an auxiliary request, the appellant overcame this rejection, but the claimed subject-matter is still...
Character Recognition – T 135/92 – 15 May 1992
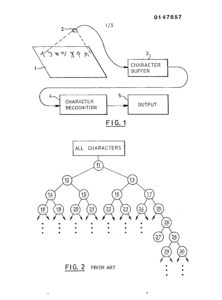
This decision concerns a method for image data. The competent chamber considers the object and solution to be technical. Object of the Invention: automatic scanning and identification of unknown characters (of image data) in a first stage, different sets of logic tests are used for the identification of characters; were...